The ongoing global pandemic has triggered uncertainty, data breaches, and long-simmering risks at the cybersecurity front. As the cyber threat landscape is evolving at an accelerated rate, businesses need to rethink their cybersecurity strategy and prioritise the implementation of the Security Operations Centre-as-a-Service (SOCaaS).
What does the current cybersecurity threat landscape look like?
With a massive expansion in internet usage and access, data breaches and falling prey to such scams are common nowadays. As the IT world witnessed a rapid push in the adoption of remote work models, the risk of insider attacks and incidents has naturally increased.
According to Forrester’s report on Predictions 2021: Cyber Security, “thirty-three percent of data breaches will be caused by insider incidents.”
And, if this wasn’t worse, the recent breach of SolarWinds has implied that implementing hardened cybersecurity measures is the new priority for organisations.
SolarWinds, a Texas-based leading provider of IT infrastructure management software, became the victim of a massive cyber intrusion. The compromised IT infrastructure of SolarWinds allowed the hackers to ambush its customers’ computer systems, including the top cybersecurity company FireEye and US government agencies such as the Department of Homeland Security and Treasury Department. This highly sophisticated cyber-attack — “SolarWinds Hack” — went undetected for months while the attackers breached into the company’s software system, Orion, and attached a malicious code. In early 2020 when SolarWinds released its software updates among its customer base (unaware of the hacked code), it provided the hackers with a secret passage to access their systems and spy on the organisations.
In the aftermath of the SolarWinds hack, which is being considered to be one of the biggest cyberattacks, the Monetary Authority of Singapore (MAS) has updated its Technology Risk Management (TRM) guidelines that all financial institutions and e-payment firms must follow.
The latest guidelines now require them to assess their technology vendors or third-party suppliers and review the security measures they practice to monitor and prevent cyber threats.
Embracing MAS Technology Risk Management (TRM) Guidelines for Combatting Cyber Threats
Now that we have a fair idea of the current threat landscape, let’s discuss the revised MAS Technology Risk Management guidelines and their impact on businesses, especially financial institutions, e-payment services, brokerage & insurance firms, and organisations reliant on third parties.
The set of guidelines aims to promote and increase the adoption of robust, reliable security practices to manage underlying technology risks.
Key Takeaways from MAS TRM Guidelines and Practices
-
- Increased roles and responsibility for the cybersecurity board of directors and senior management teams
-
- Detailed analysis and vetting of third-party vendor software, cybersecurity posture, track records, etc.
-
- Effective cyber-surveillance and information asset management, including risk identification, monitoring, review, and reporting
-
- Processes to ensure that IoT, BYOD devices are secure
Businesses need to incorporate sound and strong cybersecurity practices in their overall IT strategy to comply with the MAS TRM guidelines and other regulations. But, how do they ensure that their internal security management processes are efficient enough to detect cyber events, assess system vulnerabilities, and analyse their potential impact on the IT environment using threat intelligence?
A fully managed SOC-as-a-Service is the solution to all your cybersecurity and compliance needs.
SOC As A Service (SOCaaS) Implementation: The Need-of-the-hour for Your Business
Not having an integrated vulnerability management framework in place allows attackers to break into your internet-facing infrastructure and exploit vulnerabilities in:
-
- exposed FTP servers or RDP connections,
-
- unpatched servers and computer systems,
-
- systems with no multi-factor authentication or stolen credentials
Moreover, organisations that still operate their IT infrastructure with inefficient endpoint security practices and outmoded cyber defense systems are the potential victims of corporate-level security attacks.
Gartner recommends digital-first organisations to, “use managed security services (MSSs) to offset the cost of (in-house) 24/7 SOC operations and to fill coverage and skills gaps, either tactically or as part of the long-term strategy.”
Select a competent, scalable SOCaaS model for continuous protection of your IT infrastructure.
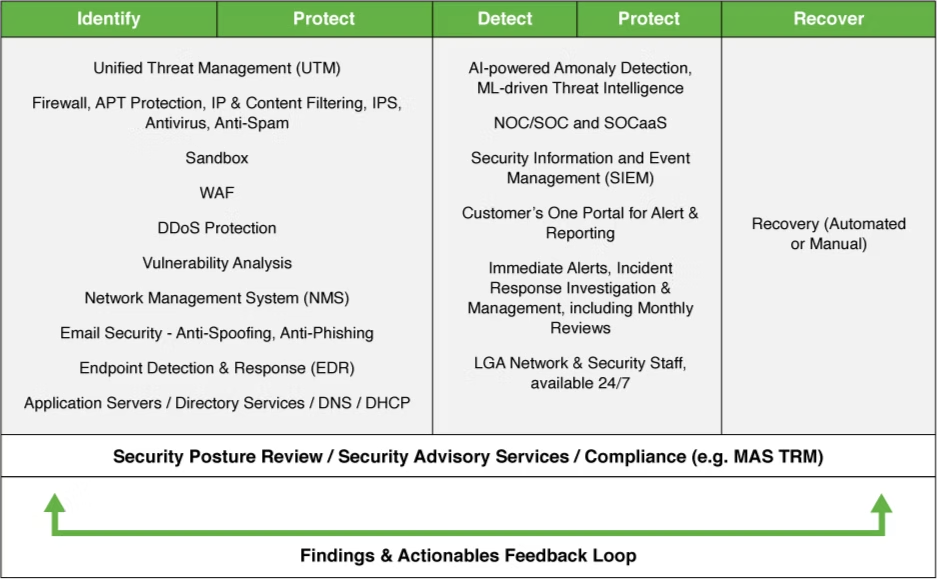
LGA SOCaaS follows the Cyber Security Framework (CSF) that helps businesses meet the latest TRM guidelines, understand and mitigate cybersecurity risks.
-
- Identify – Understand the processes, systems, data, end-users, and assets that need protection
-
- Protect – Implement appropriate safeguards to protect organisation-wide assets
-
- Detect – Implement a proper mechanism to identify the occurrence of a cybersecurity event or incident
-
- Respond – Develop techniques to contain threats before they induce harm and disruption to business operations
-
- Recover – Enforce appropriate policies and processes to restore capabilities and services impaired due to cybersecurity events
LGA’s next-generation SOC as a Service is more than just traditional managed security services that offer you rudimentary device management processes and incident alerting. Its advanced, real-time threat detection and incident response capabilities enable you to streamline the management of your security ecosystem end-to-end.
What makes this managed security solution more efficient and the right model for your organisation is its solution offerings that are tightly mapped to Cyber Security Framework’s key functions.
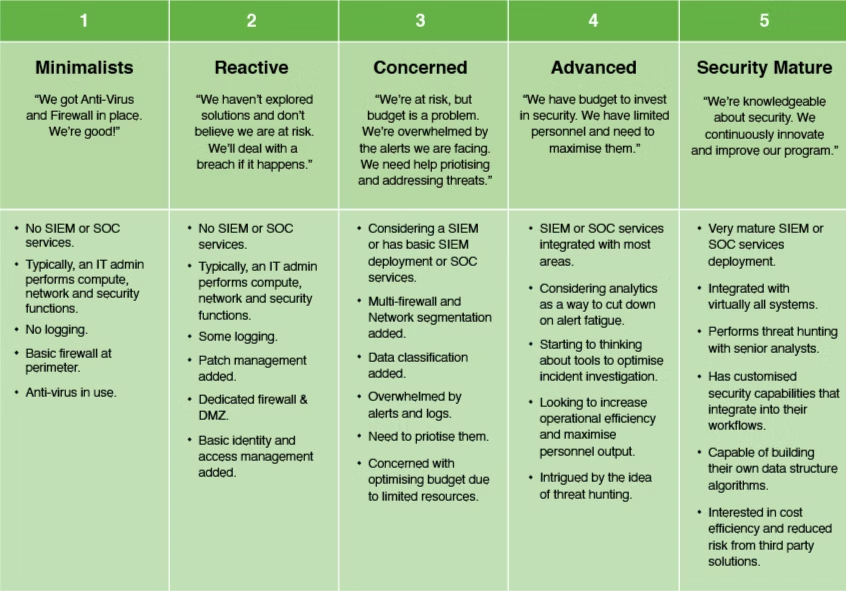
Since LGA understands that one size does not fit all anymore, its SOCaaS provides a comprehensive and flexible solution framework based on the current stage of your “Security Maturity.”
See the datasheet for more information.
In Conclusion:
The 2021 outlook of cybersecurity and its threat landscape remains complex and unmapped. Detection and response to modern-day threats will be difficult if companies don’t shift their focus to cyber threat intelligence and management.
To stay ahead of the transformational curve and have an edge in the cybersecurity battlefield, organisations must adopt an advanced SOCaaS for proactive detection, prevention, and response to emerging cybersecurity risks and vulnerabilities. LGA’s Security Operations Centre-as-a-Service fits rightly into the picture when strengthening your cybersecurity framework and posture is concerned. Protect your digital business with LGA SOCaaS today.


